The elimination of time spent on hardware upkeep and maintenance, a need for disaster recovery environment, the rise of data-driven culture where users and decision makers need the flexibility to access information instantly, are feverishly driving cloud adoption today, regardless its public, private or hybrid cloud. The recent Covid-19 pandemic, even further accelerated this migration to the cloud.
With this upwards cloud adoption trend, CIOs and CISOs are tasked with the responsibility of keeping the data safe. Not only safe when data is at-rest but also safe when it is in-motion and even when in-use.
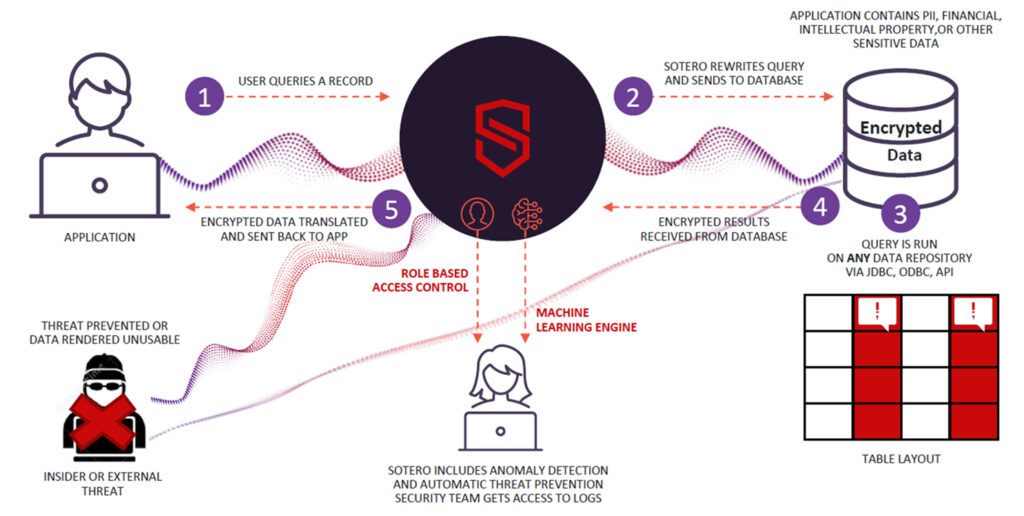
How do you get all the benefits of the cloud without the security risk and also can manage sharing of data with confidence?